Research breakthrough possible @S-Logix
pro@slogix.in
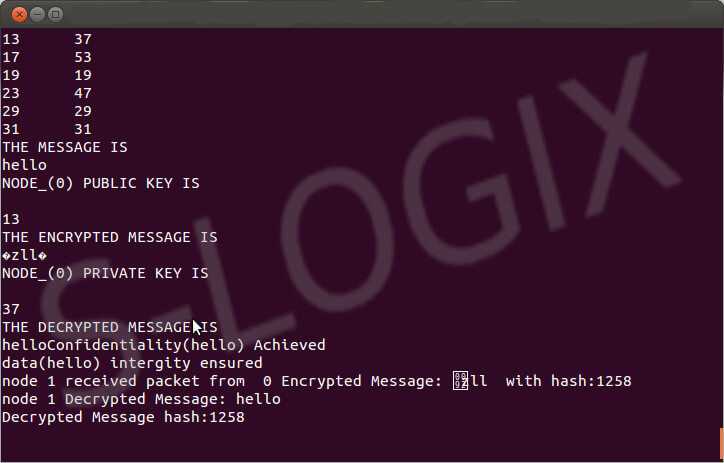
Message from the source to destination is sent in encrypted form. Even though message confidentiality is achieved through encryption, it could be modified by the intermediate attacker. Hence to ensure message integrity, hashing algorithm is applied in which encrypted message is sent along with its hash value. At the receiver end, message is decrypted and hash value computation is performed. If the received hash value and the computed hash value is same then the message integrity is ensured.
#Filename: hashing.cc
hashing () {
for(i=0; i < len; i++)
{
int mod = i % 32;
ret ^=(unsigned int) (word[i]) << mod;
ret ^=(unsigned int) (word[i]) >> (32 – mod);
}
return ret;
}