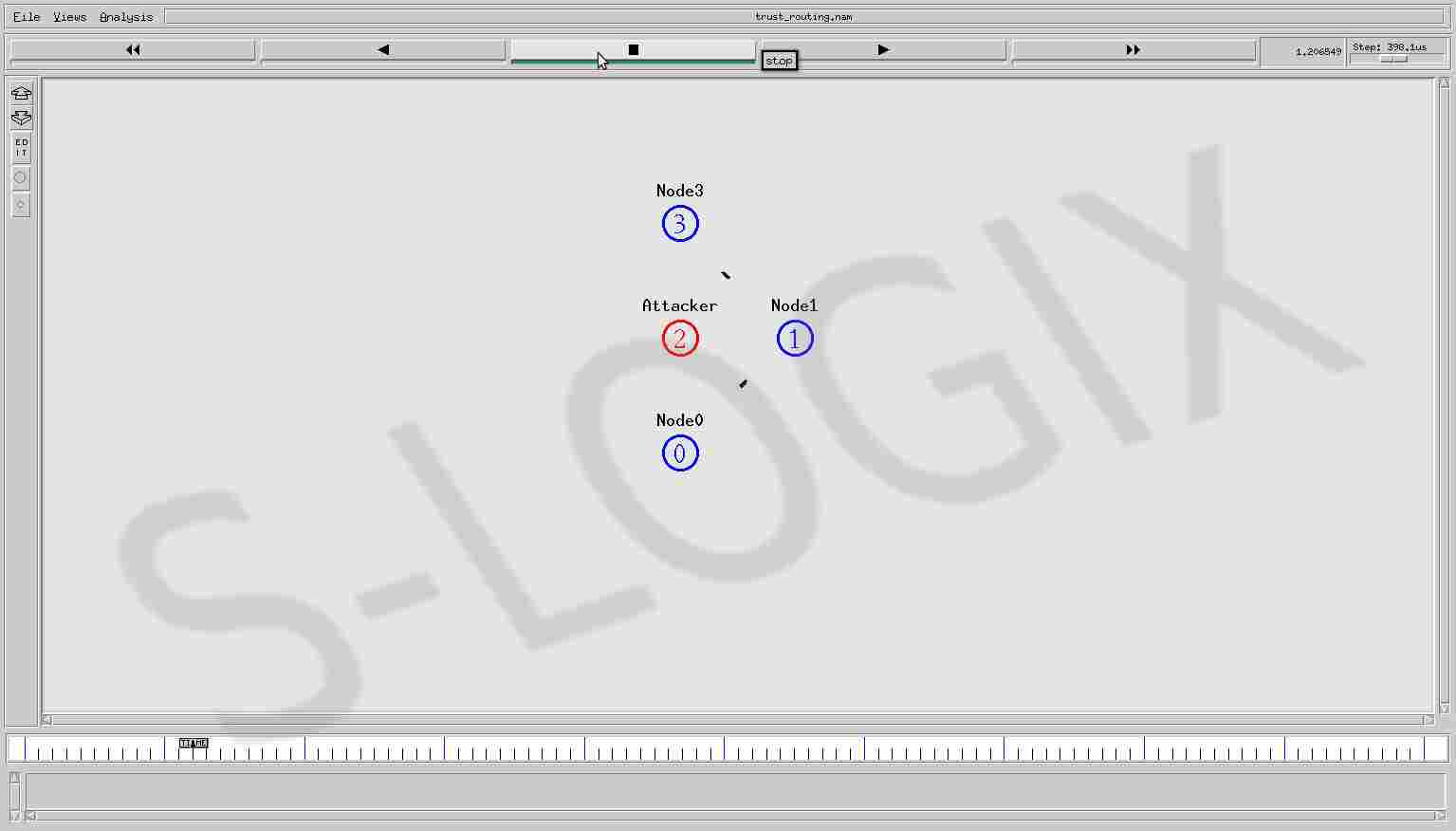
Wireless data transmission in the network is always vulnerable to various attacks such as packet dropping, misrouting, selective forwarding, and so on. If the routers involved in the data transmission process are selected on trust basis, reliability of data delivery can be achieved. In file trust_routing.tcl, behavior of the router is observed and its trust value is updated. Data transmission is carried out through the routers with high trust value. Node 2 is modeled as attacker and it is eliminated from the routing.
#Filename: trust_routing.tcl
#Model Attacker
$ns at 0.0 "[$node_($i) set ragent_] malicious"
#Compute trust and select router based on threshold
set trust($i) [expr $forwarded($i) / $received($i)]
if {$trust($i) > 0.8} {
set router $i
}