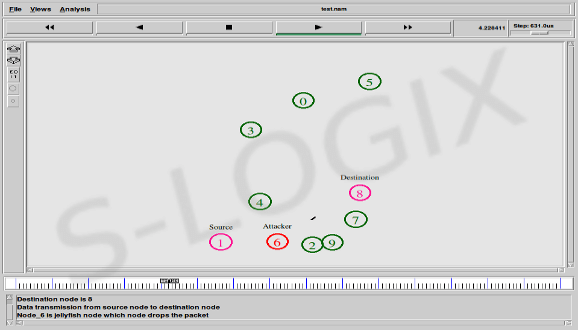
In this attack, JellyFish nodes randomly discard some packets over a specified period during communication process using TCP.
TCL part :
#*******Data Transmission from Source to Destination*****
set tcp [new Agent/TCP]
$ns attach-agent $node_($source) $tcp
set ftp [new Application/FTP]
$ftp set interval_ 0.1
$ftp attach-agent $tcp
set sink [new Agent/TCPSink]
$ns attach-agent $node_($destination) $sink
$ns connect $tcp $sink
$ns at 3.0 "$ftp start"
$ns at 3.1 "$ns trace-annotate \" Data transmission from source node to destination node\""
$ns at 4.0 "[$node_(6) set ragent_] malicious_jellyfish"
$ns at 4.0 "$node_(6) color red"
$ns at 4.0 "$node_(6) label Attacker"
$ns at 4.1 "$ns trace-annotate \" Node_6 is jellyfish node which node drops the packet \""
$ns at 15.0 "$ftp stop"
C++ part :
if (malicious_jellyfish == true) {
if (ch->ptype_ == PT_TCP) {
int x;
x = Random::uniform(0, 10);
if (x > 3) {
drop_count++;
d_count[index] = drop_count;
printf("the packet dropping node %d count %d \n",index,drop_count);
drop(p, DROP_RTR_ROUTE_LOOP);
return; //Required if you get pkt flow not specified error.
// DROP_RTR_ROUTE_LOOP is added for no reason.
}
}
}