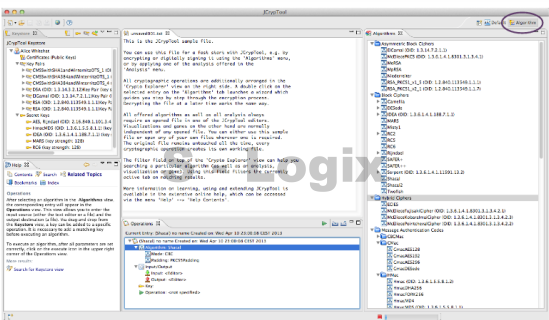
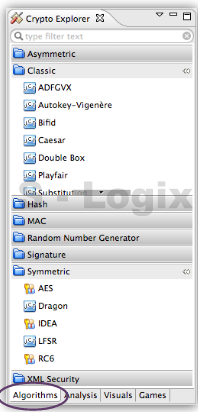
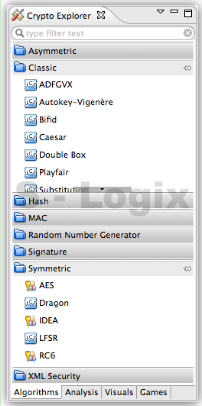
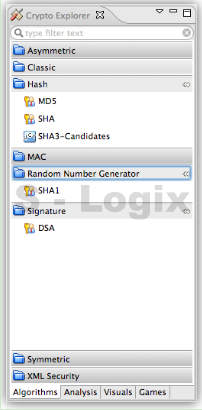
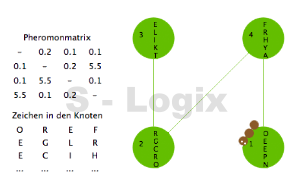
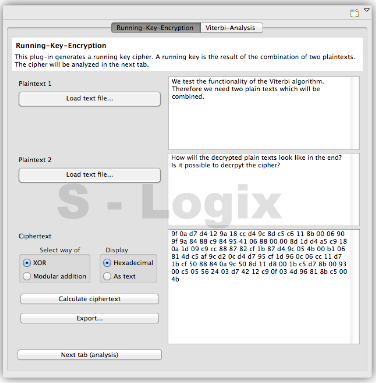
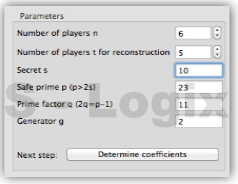
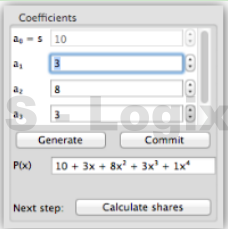
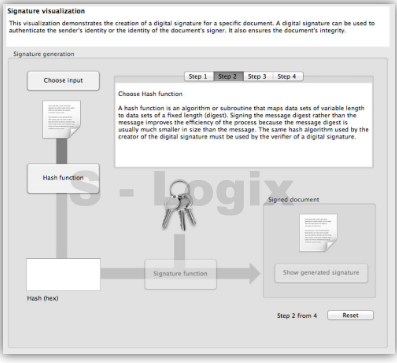
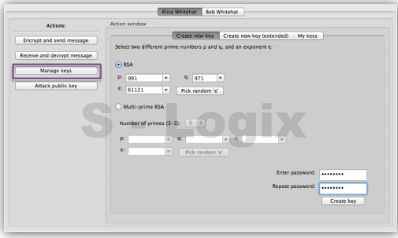
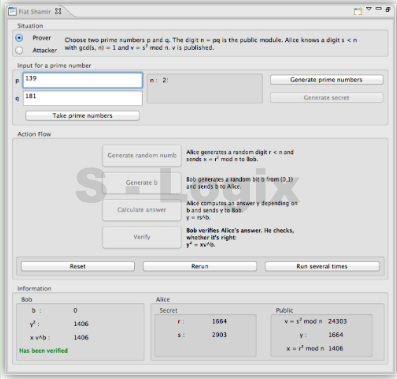
JCrypTool (Java Cryptographic Toolkit) is an open-source platform for learning and teaching cryptographic and security concepts. It provides a user-friendly interface and a wide range of cryptographic tools and algorithms for educational purposes. JCrypTool (JCT) is intended to help individuals, including students, teachers, and cryptography enthusiasts, explore and understand cryptography through interactive tutorials, experiments, and exercises.

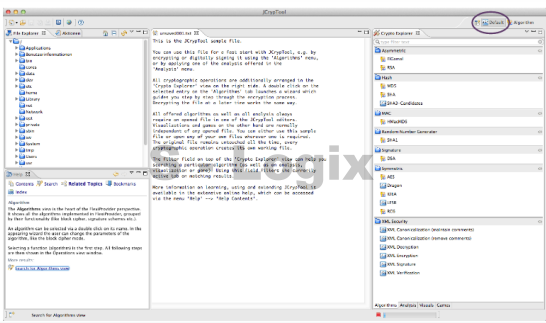
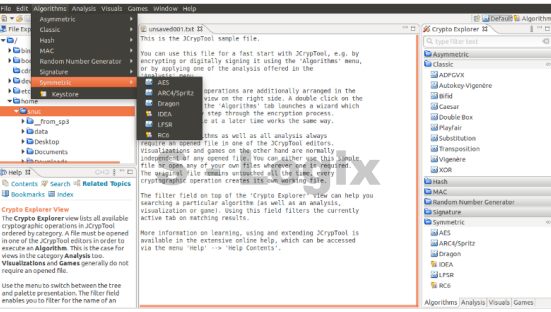
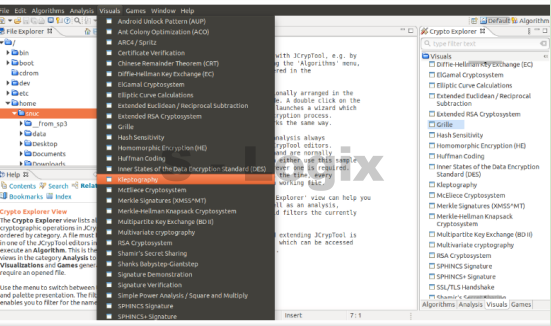
User Interface: JCrypTool provides a graphical user interface (GUI) that makes it accessible and easy to use, especially for those new to cryptography.