If the operation environment is hostile, security mechanisms against adversaries should be taken into consideration. Among many physical attacks to sensor networks, the node clone is a serious and dangerous one. Because of production expense limitation, sensor nodes are generally short of tamper-resistance hardware components; thus, an adversary can capture a few nodes, extract code and all secret credentials, and use those materials to clone many nodes out of off-the-shelf sensor hardware. Those cloned nodes that seem legitimate can freely join the sensor network and then significantly enlarge the adversary’s capacities to manipulate the network maliciously.
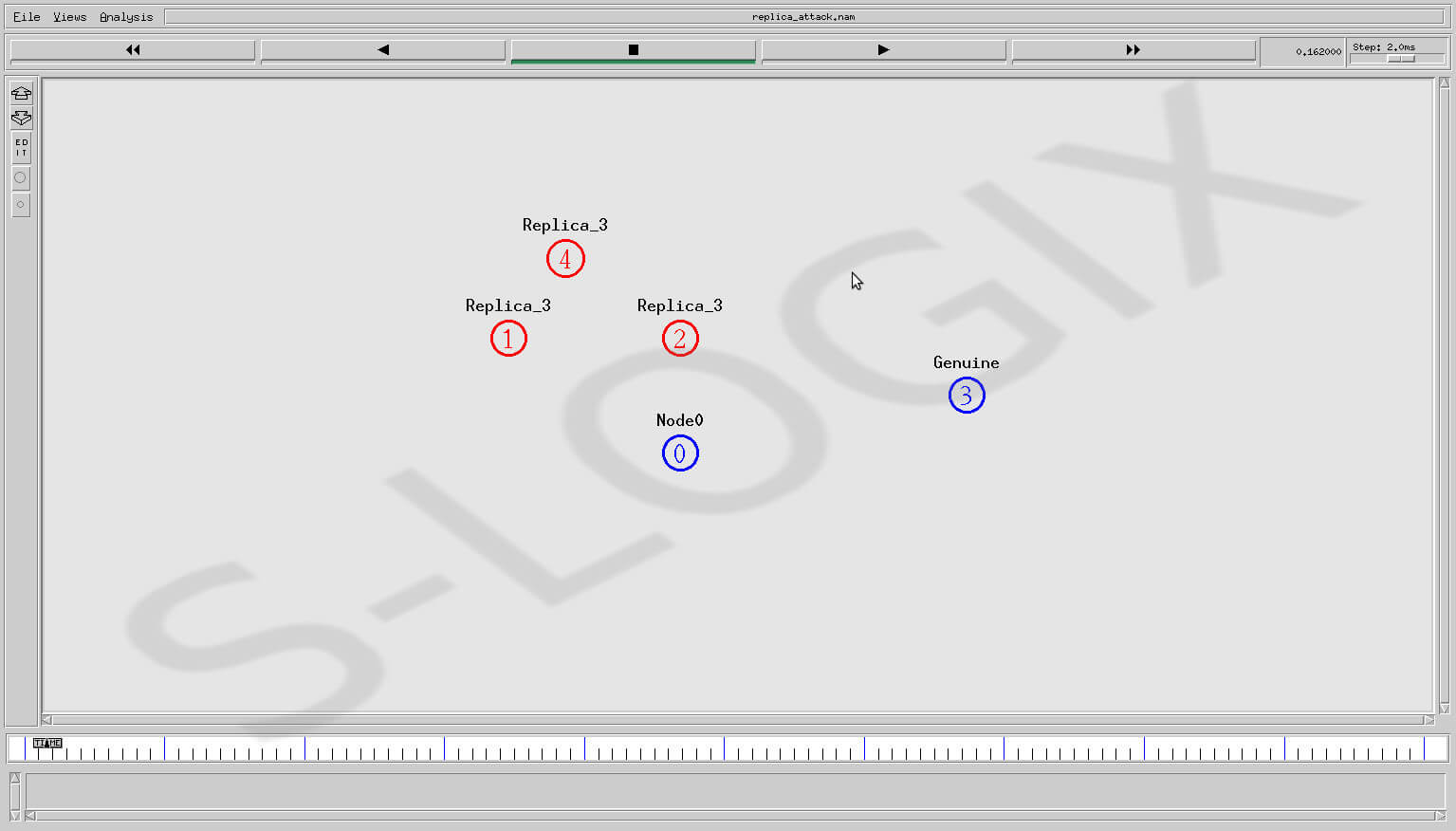
In replica_attack.tcl, nodes 1, 2 and 4 are configured as attacker vehicles and they act as a cloning of genuine vehicle 3 and send multiple messages to conversation holder.
#Filename: replica_attack.tcl
set conversation_holder 3
set replica(0) 1
set replica(1) 2
set replica(2) 4
for { set k 0 } { $k < 3} { incr k } {
set udp1 [new Agent/UDP]
$ns_ attach-agent $node_($replica($k)) $udp1
set cbr1 [new Application/Traffic/CBR]
$cbr1 set packetSize_ 512
$cbr1 set interval_ 0.5
$cbr1 attach-agent $udp1
set null1 [new Agent/Null]
$ns_ attach-agent $node_($conversation_holder) $null1
$ns_ connect $udp1 $null1
$ns_ at [expr $now ] "$cbr1 start"
$ns_ at [expr $now + 1.0] "$cbr1 stop"
}
$ns_ at $now "$ns_ trace-annotate \"Attacker Pretends like multiple vehicle and
send message to conversation holder\""
Data flow