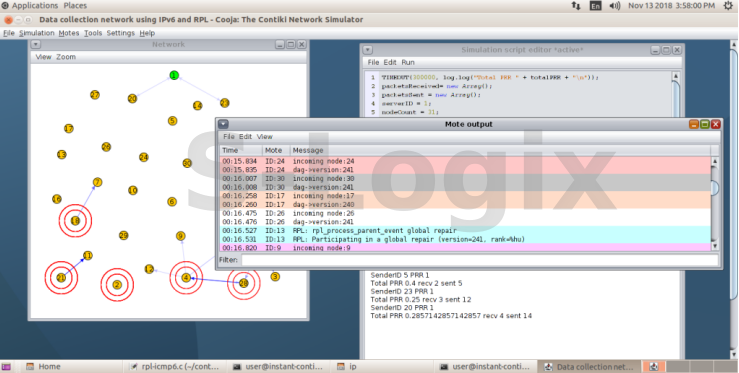
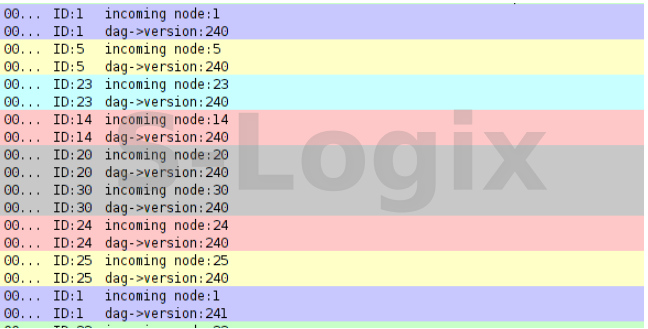
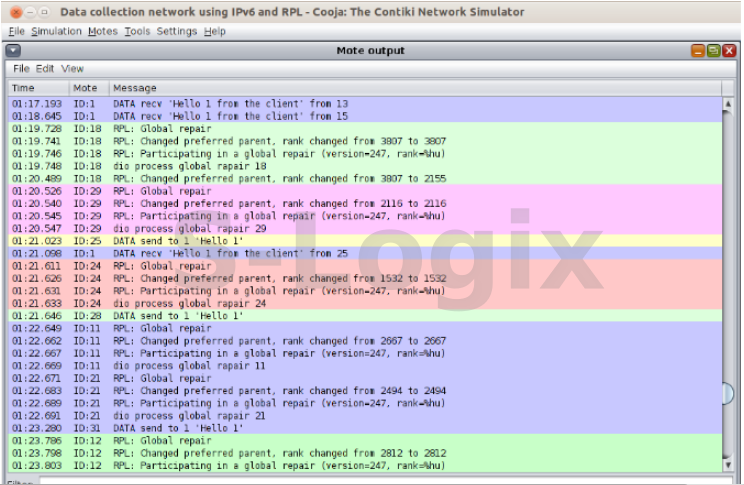
It’s an indirect attack, it Occurs when malicious node publishes a higher version number of a DODAG tree.This repair take place when network inconsistent can’t be repaired by local repair mechanisms. It’s triggered by the DODAG root incrementing the DODAG version number to initiate a new DODAG version.
Open a file to modify at location:
Home/user/contiki/core/net/rpl/
rpl-icmp6.c -
controls the input
and
output for RPL control
messages.
Modifying
in this function
to force a mote to send DIO messages
with
higher DAG version.
if (node_id == root) {
dag->version++ ;
}
Instead of dag->versionadd above code
To incremented version and provoke global
repair.
Contiki/core/net/rpl/rpl-dag.c
Create a simulation in cooja.New simulation(ctrl+n).
To create motes choose the
files at following
location:Home/user/contiki/
examples/ipv6/
rpl-udp
udp-server.c, udp-client.c
Run the simulation.
When root increasing the dag version, that case global repair occurred.